The Health Insurance Portability and Accountability Act (HIPAA) is a US law that establishes requirements for processing protected health data.
Institutions that collect or process these data in the USA and their subcontractors must comply with HIPAA if they want to avoid sanctions. For European companies in particular, HIPAA is a regulation that is difficult to understand and hard to keep track of.
This article will give you an overview and help you avoid common misunderstandings and false assumptions, making it easier to get to grips with the act.
1. What is HIPAA?
a) A law that amends the body of legislation
The Health Insurance Portability and Accountability Act (HIPAA) is a US law that added Parts 160, 162, and 164 to Title 45 of the Code of Federal Regulations, or amended them.
It is comparable to the German Digitale-Versorgung-Gesetz, which amended a lot of laws and codes, e.g., SGB V.
The texts of HIPAA are difficult to understand. This is due to
- the content,
- the abstract wording,
- the unfortunate formatting, and
- several amendments that do not appear in the original text.

The US Department of Health & Human Services has provided an unofficial consolidated version of the act.
The first version of HIPAA was passed in 1996. Since then, it has been amended and supplemented numerous times.
b) An act with several parts
HIPAA has three parts:
- Part 160 establishes general administrative requirements, including procedures of official bodies and penalties.
- Part 162 also contains administrative requirements. However, in addition it establishes requirements for interoperability, such as healthcare provider identification and data exchange.
- Part 164 is the part most people refer to when talking about HIPAA. It regulates “Security and Privacy.”
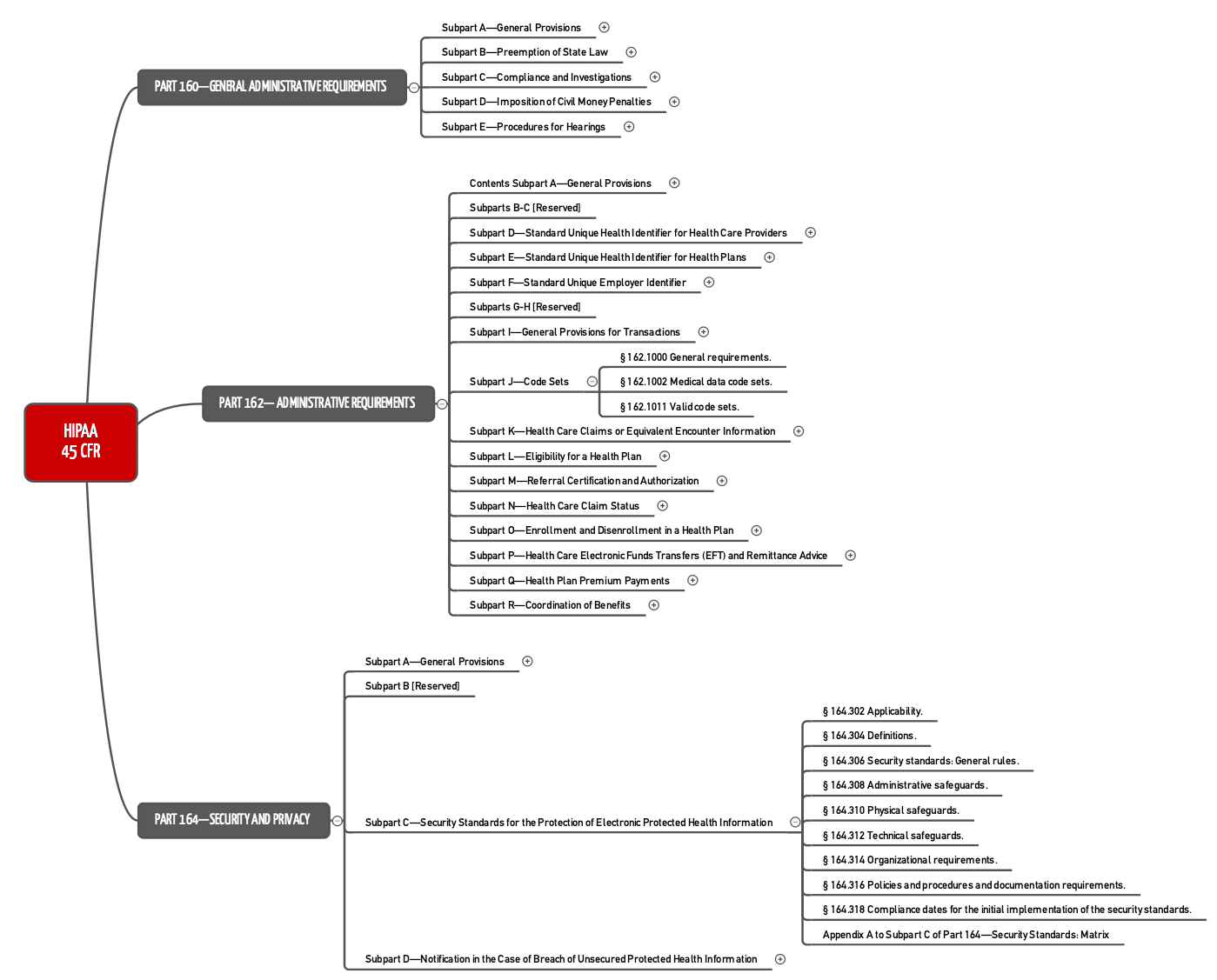
Part 164 establishes requirements for the protection of electronically processed health information and for the procedure to follow if that protection has been breached.
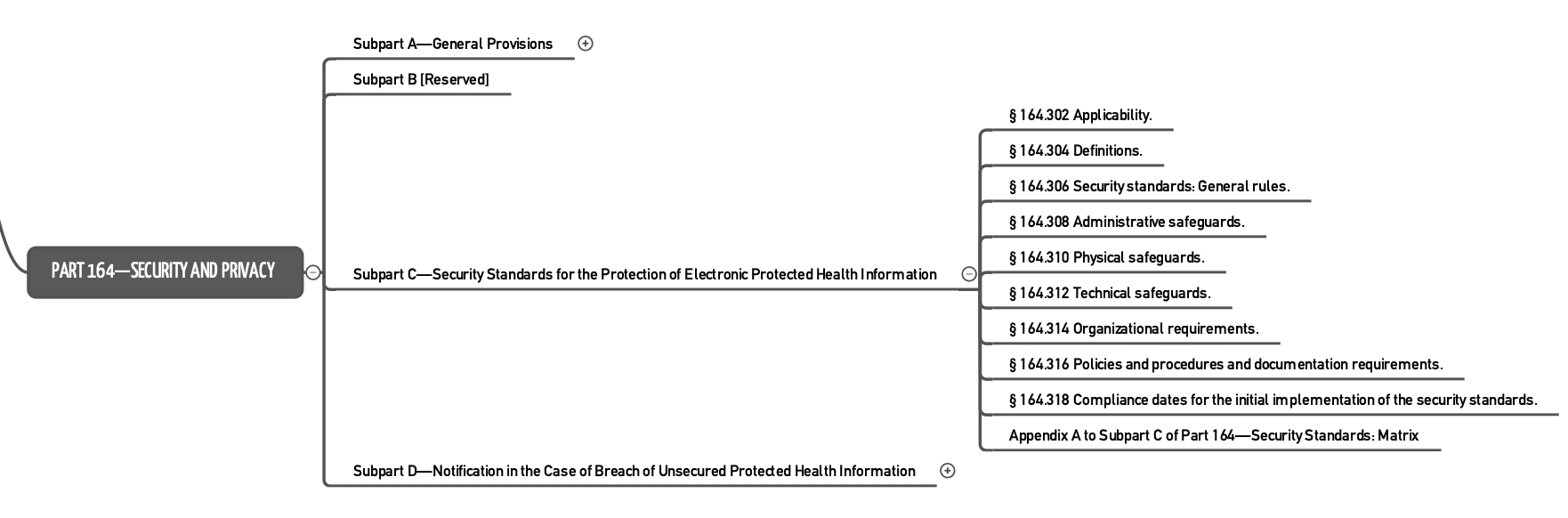
c) HIPAA is an act that establishes several rules
We often talk about HIPAA Rules. These are not additional requirements but, in fact, correspond to certain parts of the act:
| Rule | HIPAA | Subject |
| Security Rule | Part 160 and Part 164: Subparts A and C | Strictly speaking, data protection is part of the next rule. |
| Privacy Rule | Part 160 and Part 164: Subparts A and E | Data protection |
| Enforcement Rule | Part 160: Subparts C, D, E | Official authority enforcement rights and obligations |
| Breach Notification Rule | Part 164: §§ 164.400-414 | Breach reporting obligations |
| Omnibus Rule | This is another amendment to HIPAA included in the 2013 HITECH Acts. It concerns contracts with business partners such as cloud service providers. |
In these parts, HIPAA establishes:
- Which data have to be protected
- What exceptions there are, i.e., which data may or must be passed on
- The data protection requirements that must be met
- The measures organizations must take in the event of a breach of confidentiality
- The measures the authorities take in such cases
2. Who is affected by HIPAA?
a) Organizations affected
According to the definition provided, health information is only information that is created or received by certain organizations.
health care provider, health plan, public health authority, employer, life insurer, school or university, or health care clearinghouse
Source: 45 CFR Part 160,103
What is meant by “health plan” is also clarified in a definition:
an individual or group plan that provides, or pays the cost of, medical care (as defined in section 2791(a)(2) of the PHS Act, 42 U.S.C. 300gg-91(a)(2)) […]”
Source: 45 CFR Part 160,103
This means that neither software manufacturers nor cloud service providers fall under this definition. However, a manufacturer’s software must meet the above requirements if he wants his software to be used by the institutions named.
A service provider, such as a cloud service provider, is considered one of the “business associates” who are subject to the same requirements as the above organizations.
b) Data affected
HIPAA refers to Protected Health Information (PHI). This is similar to what the GDPR calls personal data. Examples include names, contact details, identifying numbers, medical data (the GDPR calls this “data concerning health”), photos, and invoices.
3. What does HIPAA require?
Like European laws and regulations such as the GDPR and the BSI guidelines, HIPAA requires technical and organizational measures.
… in terms of infrastructure and systems
Some of these measures result in infrastructure and IT system requirements:
- Physical safeguards to restrict access to infrastructure. This can be achieved with, e.g., locked rooms and locked-up IT systems. This prevents theft as well as unauthorized access.
- Logging of activities on the systems, including system use and modifications
- Unique user identification, authentication, and authorization
- Providing an option for emergency access to data
- Automatic logging off of users
- Data encryption
- Protection and verification of data integrity (also in the event of transmission)
- and many more
… in terms of organizations / manufacturers
A lot of the measures are organizational in nature. For example:
- Backup procedures must be established and reviewed.
- Access to data for testing must be regulated.
- Subcontractors must be obligated to comply with data protection regulations.
- Who can carry out which activities on the systems under which circumstances must be regulated. This applies to the use, modification and maintenance of these systems.
- How removable storage media are handled and how they should be disposed of must be described.
- The people responsible must establish procedures for granting and revoking authorizations.
- There are certain requirements regarding the choice and assignation of passwords.
4. What are the common misconceptions?
a) There are HIPAA-compliant or even HIPAA-certified systems
Just as software cannot be ISO 13485, IEC 62304, or GDPR-compliant, it cannot claim to be HIPAA-compliant or even HIPAA-certified.
However, software can offer all the conditions required for a manufacturer to achieve HIPAA compliance. For example, if the software does not allow data encryption, HIPAA-compliance would not be possible. Hence, there is no HIPAA-certification for products.
b) There are HIPAA-certified organizations
Strictly speaking, there is no such certification for organizations. However, there are companies/organizations that conduct audits and then issue a certificate. But this is not based on an official accreditation.
Sometimes the term HIPAA certification is used in the context of personal certifications. This means that an individual has passed an exam where they demonstrated their HIPAA competency.
c) It’s only about data protection
HIPAA is often understood as being the US’s health data protection requirements.
This idea is not wrong but it’s not the whole picture. As the name of the act suggests, it also concerns the “portability” of data, i.e., interoperability.
However, these requirements are so high level that they cannot beused to create a specification for interfaces. At least, HIPAA already specifically mentions semantic standards such as the ICD-9-CM catalog for diagnoses and treatments and CPT codes for services such as laboratory and radiology.
5. FAQs
a) How does HIPAA differ from the GDPR?
Both HIPAA and the GDPR are laws relating to data protection. However, they differ in many respects:
- HIPAA is not limited to data stored electronically.
- Unlike the GDPR, HIPAA “only” affects health data.
- HIPAA regulates much more than just data protection issues. HIPAA also regulates interoperability and the rights of official bodies.
- HIPAA differentiates and defines genetic information a lot more precisely than the GDPR.
- The GDPR only talks about technical and organizational measures. HIPAA imposes more specific requirements.
Please also refer to our articles on IT security in the healthcare sector and data protection requirements for DiGA.
b) Where can I learn more on the topic?
There is a lot of money to be made from HIPAA. So, be careful about where you get your information from. A good place to start is the official website of the US Department for Health and Human Services (HHS).
- An initial introduction with links to additional information can be found on the HHS’s website
- The combined text of the act can be found here, and the corresponding PDF here
- The Center for Disease Control and Prevention has published FAQs on HIPAA
- It is not an official site, but the Compliance Junction website offers a good introduction (“for dummies”)
- A commercial provider also offers a good initial overview in German
6. Conclusion and summary
The requirements of HIPAA are very broad and go beyond data protection. Whether it is wise to mix such disparate aspects is another matter.
Anyone who already has certification, e.g., according to ISO 27001 or BSI, has (almost) completely fulfilled HIPAA’s data protection/IT security requirements.
Conformity can only be achieved through organizational and technical measures, ideally through an IT security management system.
HIPAA should hold no terrors for BSI or ISO 27001-certified organizations. However, the US authorities consistently crack down on breaches.
The Johner Institute supports companies in setting up integrated quality and IT security management systems (QMS and ISMS). This enables companies to achieve ISO 13485 and ISO 27001 compliance quickly, without redundancies and unnecessary overhead, and thus meet the requirements for developing and operating IT solutions in the healthcare sector.
Change history
- 2023-12-20: Links to articles on security and data protection added
- 2022-04-05: First version