We have known how vulnerable IT security is in the healthcare sector since February 2016, when the IT infrastructures of many clinics were brought to a standstill by a simple virus attack. As a result, the authorities are paying closer attention to ensuring that not only clinics but also manufacturers guarantee the IT security of their (medical) devices.
This article will give you an overview of what hazards IT security in the healthcare sector and what you can and must do about them. This will help you avoid regulatory trouble and develop and operate devices safely.
Update: The latest BSI publications have been added to chapter 3. a). This gives you a quick overview of 120 pages.
1. Particularities of IT security in healthcare
Threats to IT security are not limited to healthcare. Yet there are some particularities to consider:
- Human lives are threatened
In contrast to attacks on private individuals’ or many corporate infrastructures, attacks on IT infrastructures in healthcare (e.g., of clinics) pose a threat to humans, more precisely to patients. If a clinic’s IT breaks down, just as happened recently, no more patients can be admitted, and surgeries have to be postponed. If medical ventilators of an intensive care unit are targeted, patients can die within minutes. - Specific regulations must be complied with
Threatening IT security in healthcare also means threatening the protection of highly confidential personal data on health. For this reason (but not for this reason alone), specific regulations for operators of healthcare facilities and for medical device manufacturers exist, which you can read more about in the following section. - Many clinics operate unprofessionally
There are only a few other sectors outside the healthcare sector that invest so little money in IT security. In line with the motto “you get what you pay for”, many IT departments of clinics are understaffed and poorly trained. IT security is further undermined by adventurous IT infrastructures and the high extend of partly uncoordinated outsourcing to all kinds of actors (service providers for printers, firewalls, PCs and hotline, manufacturers of IT systems and medical devices). - Manufacturers act irresponsibly
Manufacturers, too, are responsible for insufficient IT security. Among the reasons are:- “Historically grown” system and software architectures
- Poor understanding of the menace to IT security caused by total integration of IT and medical engineering
- Lack of will to systematically analyze and manage IT security as part of risk management
- Lack of willingness to assume responsibility not only for their own product but also for the product in the context of a clinic network
Would you like to know how to make your IT systems safer? The experts at the Johner Institute will be happy to advise you.
2. IT security regulatory requirements in healthcare
a) Requirements for manufacturers
In contrast to the USA, the European judicial area knows only a few specific standards for addressing IT security of medical devices.
EU law and national laws
- Under MDR Annex I, 17.2, the MDR explicitly requires software development to be “state-of-the-art”. This includes IT security. Now, manufacturers must define requirements regarding measures by operators about IT security. The MDR even internalizes the demand for data protection.
- The MDCG has published the 2019-16 guidelines, in which the Medical Device Coordination Group explains in more detail how it intends to implement the MDR and IVDR’s IT security requirements.
- The DiGAV calls for IT security and data protection. The article on the DiGAV also mentions that the BfArM has published guidelines and FAQs on this subject, which address the use of US cloud providers, among other things.
- The EU has included IT security in the Radio Equipment Directive (RED). IT security is, therefore, a mandatory requirement for the CE marking of devices with a radio module. However, according to MDR/IVDR, medical devices are exempt from the corresponding regulations (Art. 2 Para. 1 Delegated Regulation (EU) 2022/30).
- The new Cyber Resilience Act is also not applicable to medical devices, according to MDR and IVDR. However, manufacturers can consider it an additional guideline for the state of the art.
- At the end of 2022, the EU launched a new directive called NIS2. It must now be transposed into national law within 21 months. The new directive does not yet have any direct consequences for manufacturers. This is also because the member states first have to transpose the changes into national laws. However, it is obvious that medical device manufacturers must ensure the IT security not only of their devices, but also of their organization.
Requirements of the national authorities and notified bodies
- The CyberMed expert group explains how manufacturers should complete the “Manufacturer Disclosure Statement for Medical Device Security (MDS2)” in the 2019 guidelines for using the MDS2, which are available on the BSI (German Federal Office for Information Security) website.
- The BSI has published a document on cyber security requirements for network-enabled medical devices.
- The BSI has also published the technical guideline BSI TR-03161: Security Requirements for Digital Health Applications. The BSI guideline, in turn, refers to other specifications, although these are not specific to medical devices:
- BSI Standard 200-1, BSI Standard 200-2, BSI Standard 203
- BSI IT baseline protection compendium
- BSI TR-02102-1: Cryptographic procedures: Recommendations and key lengths
- BSI TR-02102-2: Cryptographic procedures: Use of TLS
- TR-03107-1: Electronic identities and trust services in eGovernment Part 1
- The notified bodies have developed their guideline on IT security based on the Johner Institute’s guideline. As this is published and used by the notified bodies, it is a must-read, at least for German manufacturers.
Standards
- In its latest version, ISO 13485:2016 was amended to include protection of confidential data as well as the establishment and review of requirements for associated medical devices
- IEC 60601-1 demands risks in consequence of a “lack of data security, particularly vulnerability to tampering, unintended interaction with other programs and viruses” to be managed.
- IEC 60601-4-5 is also specific to medical devices. It references the IEC 62443 standard, which means that its catalog of requirements is very extensive.
- With Amendment I (2016) of IEC 62304, the standard requires that software requirements include IT security requirements.
- Risk management (e.g., compliance with ISO 14971) has always had to address all risks, including those caused by a lack of IT security, such as cyber-attacks.
- The cybersecurity standard IEC 81001-5-1 deals with how IT security must be taken into account in the software life-cycle.
- ISO 27002 describes almost 100 controls (security measures). It was significantly revised in 2022. A new edition of ISO 27001, already available as FDIS, is also expected at the end of the year.
Regulatory requirements in the USA and other countries
- In the USA, operators must comply with the requirements of HIPAA.
- The FDA has published specific requirements in four(!) guidance documents on the topic of cybersecurity.
- The FDA also references AAMI 57 on IT security risk management in accordance with ISO 14971.
- It also recognizes UL 2900-2-1 as a standard for IT security.
- Health Canada followed suit in December 2019 and also published a draft guidance “Premarket Requirements for Medical Device Cybersecurity“.
- In April 2020, the IMDRF also published a guideline on cybersecurity.
- In April 2022, the FDA published a draft guidance Cybersecurity in Medical Devices: Quality System Considerations and Content of Premarket Submissions Draft Guidance for Industry and Food and Drug Administration Staff.
- The FDA has commissioned MITRE (a non-profit organization) to develop a “playbook.” This “Medical Device Cybersecurity Regional Incident Preparedness and Response Playbook” is now available.
Read more about the FDA’s Cybersecurity Guidance Documents and the IT security guideline (German) published by the Johner Institute and several TÜVs here.
DiGA manufacturers should read the article on security and data protection for DiGA (German). It summarizes all the regulatory requirements relevant to DIGA and saves you from having to search through 100 pages of regulations. This also includes BSI TR 03161.
b) Requirements for operators
EU regulations, EU directives, German laws
Many people are unaware of EU Directive 2016/1148 “concerning measures to ensure a high common level of security of network and information systems across the Union.” It is also known as the NIS Directive (The Directive on security of network and information systems).
This directive explicitly mentions “healthcare facilities (including hospitals and private clinics)” in Annex II. It was transposed into national law as the BSI Act (see above).
Operators must also guarantee data protection. IT security is a necessary but not a sufficient prerequisite for this. The General Data Protection Regulation forms the basis.
German laws and regulations
In addition, there are national provisions such as the BSI Act and further demands by the German Federal Office for Information Security (BSI) regarding healthcare. In the course of the national critical infrastructure protection strategy (KRITIS strategy), the IT Security Act, too, was put into effect, which explicitly addresses healthcare.
Due to increasing cross-linkages, medical device manufacturers increasingly become operators. Therefore, the MPBetreibV and comes into effect, which requires secure operation.
Standards
IEC 80001 is a standard describing risk management regarding the operation of IT systems in the healthcare sector. Data and system security (IT security) is one of the three explicit protection targets. In this context, especially IEC 80001-2-8 („Application guidance — Guidance on standards for establishing the security capabilities identified in IEC 80001-2-2“) is relevant.
The German Hospital Federation has published a guideline entitled “Sector-specific safety standard for healthcare in hospitals” (only available in German).
c) Sector-independent requirements
The following laws, too, are directly related to IT security:
- Law on Control and Transparency in Business (KonTraG)
- Criminal Code: Sec. 202b Data Interception, Sec. 263a Computer Fraud, Sec. 303a Data Alteration and Sec. 303b Computer Sabotage
This article provides an overview of the relevant data protection regulations.
3. Examples of IT security breaches
A contribution by Doccheck (only available in German) offers an overview of IT security problems in healthcare. AAMI reports that the RansomWare attacks in May 2017 were also a wake-up call for the FDA, which calls attention to the vulnerability of IT systems in healthcare.
Cave: IT security is the extent to which information availability, integrity, and confidentiality are protected. IT security is more than just protection against cyber attacks.
a) Medical device manufacturers
Obviously ignoring requirements of risk management and of the FDA Cybersecurity Guidance, new menaces caused by medical devices disregarding elemental security standards are recurring.
- As repeatedly reported by heise.de [1; 2] and hextech.com, infusion pumps by Hospira exhibit a fatal Telnet vulnerability.
- Thousands of medical devices are vulnerable to attacks via the internet, as consistently reported by heise.de and golem.de [3], [4].
- Manufacturers’ sloppiness when writing and updating firmware is an increasing problem.
- The FDA has issued several warnings about active implants from Medtronic where communication is unencrypted and/or not authorized.
BSI: Cyber security assessment of networked medical devices
The BSI’s systematic evaluation entitled Cyber Security Assessment of Networked Medical Devices (only available in German) is also interesting. The authority examined the following product classes:
- Implantable pacemakers and defibrillators and their equipment
- Insulin pumps
- Ventilators
- Infusion pumps
- Patient monitors
As an output, the BSI concludes:
A total of more than 150 vulnerabilities were reported to manufacturers as part of the project. The inspection revealed that the vulnerabilities were often to be found in the accompanying infrastructure but rarely in medical devices. […] It is pointed out that the output of the IT security tests may have been distorted or influenced. As manufacturers’ participation in the project was voluntary, it was expected that those manufacturers with a certain level of maturity in their IT security processes would most likely cooperate.
The security assessments also showed that the IT security situation varies greatly from manufacturer to manufacturer and depends heavily on the maturity level of the individual manufacturer.
BSI
Manufacturers should benefit from these documents and
- review whether their own devices are affected by the same defect;
- take this document into account in their post-market surveillance;
- review the recommended measures for avoiding vulnerabilities to determine whether they are applicable in their own company (“preventive action”);
- adopt the methods used to detect vulnerabilities in your arsenal if necessary. The BSI even lists methods for reviewing apps and web-based systems, although these were not the focus of the study.
BSI: eCare digitalization in the care sector
The BSI’s evaluation is an exciting read. Even the market overview is helpful. The networked systems range from home emergency call systems to smart beds, sleep monitoring, and networked heated blankets.
The output is a bit disappointing:
In summary, considering the high need for health data protection, the IT security level found can be rated as poor to very poor. This can be explained, among other things, by the fact that moderate to severe vulnerabilities were uncovered in all the devices examined. It should also be noted that the depth of testing […] can be described as low and by no means corresponds to complete penetration tests or a security evaluation.
BSI: “eCare – Digitalization in care. Current market analysis and IT security assessment.”
At the very least, the devices are suitable as poor role models and give manufacturers an idea of
- how the BSI investigates when it only carries out superficial checks,
- what minimum requirements the BSI sets,
- which errors manufacturers must not make under any circumstances.
b) Health insurance providers
In several articles, I have expressed my concern that it is only a matter of time until hospitals and chains of clinics are blackmailed by data thieves, too. Unfortunately, I forgot one major participant of the healthcare system open to blackmail: health insurance providers. This has happened now, as reported by Süddeutsche and Spiegel [7].
c) Hospitals
Cyberattacks
IT security in healthcare is increasingly exposed to threats since hackers have realized the value of data [9].
Often, hospitals are not the targeted victims of cyber attacks. Rather, their badly maintained IT infrastructure with outdated and unpatched operating systems are as helpless as an open barn door in the face of attackers.
- In February 2016, computer virus Locky crippled several clinics in North Rhine-Westphalia. For example, rp-online and heise.de (only available in German) reported on this. One commentator wrote that not two, but 48 (!) clinics were affected. An expert from Kaspersky confirmed those weaknesses (article published in KH-IT Journal (only available in German)).
- Those attacks are not limited to Germany. According to Inquisitr, a hospital in California had to pay millions in ransom.
- In May 2017, hospitals are again targeted, especially the UK healthcare system NHS [10, 11] This time, the virus is called “Wanna Cry”.
Overview of the number and causes of data breaches
The U.S. Department of Health and Human Services publishes and continuously evaluates security breaches in the healthcare sector. The analyses show that the number of incidents is constantly increasing.
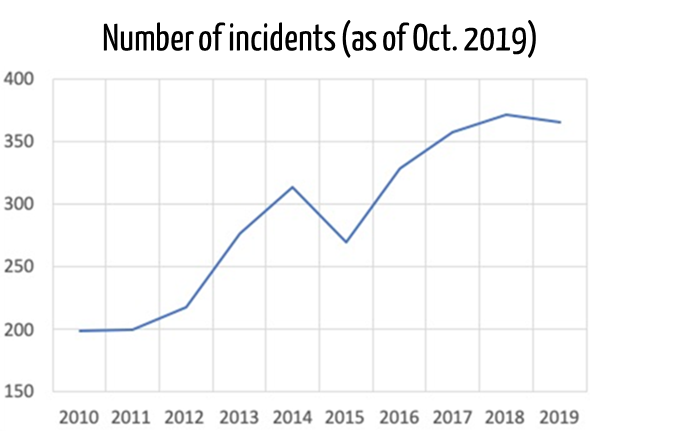
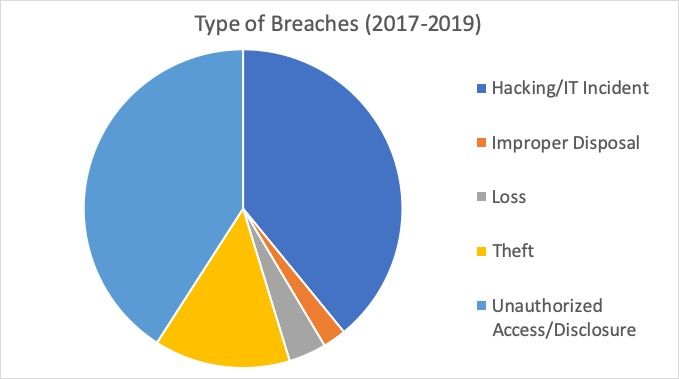
The authority has also investigated the types of attacks:
Data leaks due to hacking have increased continuously:
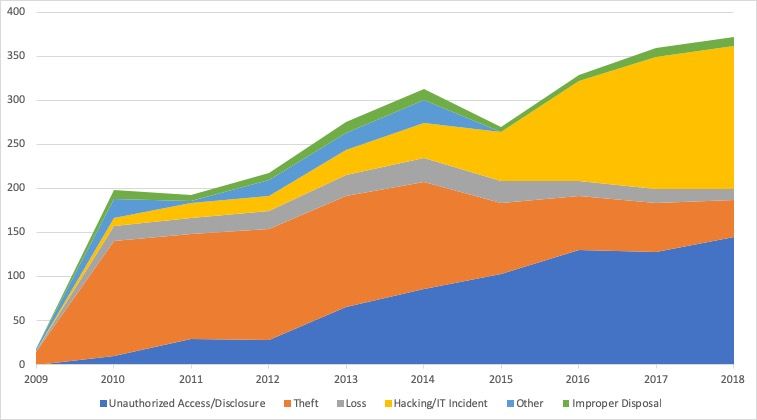
Nevertheless, it must be clear that many of the healthcare sector’s IT security problems are not due to malicious attacks from outside. Rather, negligence on the part of hospitals and medical practices causes data to be “leaked.” In September 2019, for example, millions of radiology image data were unprotected online [source].
Government agencies
It’s not just conspiracy theorists who are venting about what the NSA is using or can use because healthcare IT security has so many gaps. Our article on IT security (independent of the healthcare sector) will be helpful for more information.
The NSA is also partly to blame for the Wanna Cry attacks: it had recognized the security gap in Windows and exploited it for intelligence activities. It had not even reported the vulnerability to Microsoft when the spying tools were reported.
d) Threats
The ECRI Institute has compiled the greatest hazards for patients in the document Top 10 Health Technology Hazards for 2018. This includes several hazards that affect IT security (highlighted in bold).
- Ransomware and Other Cybersecurity Threats to Healthcare Delivery Can Endanger Patients
- Endoscope Reprocessing Failures Continue to Expose Patients to Infection Risk
- Mattresses and Covers May Be Infected by Body Fluids and Microbiological Contaminants
- Missed Alarms May Result from Inappropriately Configured Secondary Notification Devices and Systems
- Improper Cleaning May Cause Device Malfunctions, Equipment Failures, and Potential for Patient Injury
- Unholstered Electrosurgical Active Electrodes Can Lead to Patient Burns
- Inadequate Use of Digital Imaging Tools May Lead to Unnecessary Radiation Exposure
- Workarounds Can Negate the Safety Advantages of Bar-Coded Medication Administration Systems
- Flaws in Medical Device Networking Can Lead to Delayed or Inappropriate Care
- Slow Adoption of Safer Enteral Feeding Connectors Leaves Patients at Risk
Play it safe with a pentest from the Johner Institute! You can find more information here.
4. Implementation of IT security
Please refer to the IT security guideline published by the Johner Institute, TÜV Süd, and other notified bodies. It provides step-by-step instructions for ensuring IT security throughout the product life cycle.
The Johner Institut team helps manufacturers introduce ISO 27001-compliant Information Security Management Systems (ISMS) quickly and effectively. If you are interested, contact the Johner Institut, e.g., via the contact form. In a free meeting, you will learn how the introduction of an ISMS works, how long it takes, and what costs are involved.
Change history
- 2023-02-17: HIPAA requirements linked
- 2022-12: New legal requirements added
- 2022-09: Notes on the EU Cyber Resilience Act and the ISO 27000 family added
- 2022-06: Section with legal requirements supplemented by draft of the new FDA Guidance Document and IEC 80001-5-1
- 2022-02: Notes on requirements for IT security in the Radio Equipment Directive (RED) added
- 2021-02: BSI publications added to section 3.a); the large number of regulatory requirements in section 2.a) better organized with subheadings