On November 21, the Johner Institute, together with TÜV SÜD, TÜV Nord, and with the support of Dr. Heidenreich (Siemens), published a guideline on IT security specifically for medical device manufacturers.
Who the IT Security Guideline is aimed at
The guideline is aimed at all manufacturers of medical devices (persons placing on the market, service providers). It should especially be read by:
- system/software developers and architects
- (software) testers
- product managers
- quality managers
- regulatory affairs managers
It is also explicitly aimed at auditors, reviewers of technical documentation, and authorities.
Operators such as hospitals should at least take the IT Security Guideline into account if they configure or even manufacture medical devices themselves.
Where to find the IT Security Guideline
The guideline is available free of charge:
- The “official” version can be found as a markdown document in the Git repository “IT Security Guideline”.
- Contact us to request the guideline in a different format, e.g., Word or Excel.
Would you like to know how you can make your IT systems more secure? The experts at the Johner Institute will be happy to advise you!
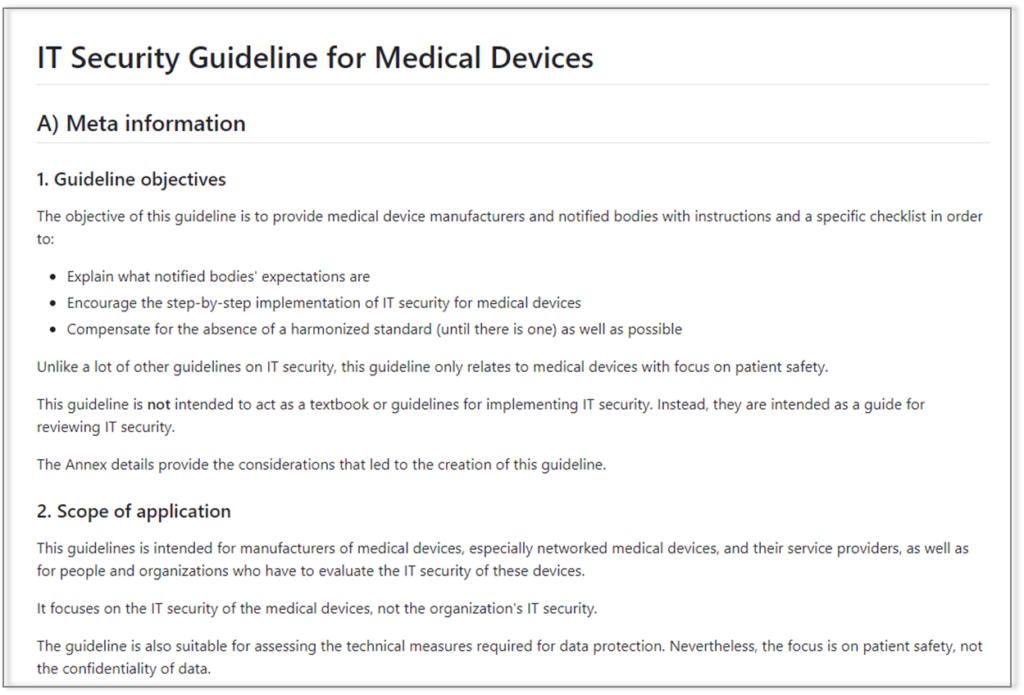
What characterizes the guideline
The authors have pursued the following objectives when writing:
- The requirements are easy to understand.
- The review of the requirements can be carried out without any doubt.
- The requirements are feasible and sensible and, therefore, conducive to IT security.
- They are – as far as necessary and possible – specific to medical devices.
- The requirements reflect the state of the art.
- This makes it easy for manufacturers to derive procedures, work instructions, and product specifications.
Layout and structure of the guideline
The IT Security Guideline comprises around 150 requirements. These are sorted according to priorities and life cycle phases.
Life cycle phases
The IT Security Guideline is divided into chapters as follows:
- Process requirements
- Requirements for the product process
- Intended purpose and stakeholder requirements
- System and software requirements
- System and software architecture
- Implementation and development of the software
- Evaluation of software units
- System and software tests
- Product release
- Requirements for the post-development phase
- Production, distribution, installation
- Post-market surveillance
- Incident response plan
- Requirements for the product process
- Product requirements
- Preliminary remarks and general requirements
- System/software requirements
- System/software architecture
- Accompanying materials
The requirements for the processes should be reflected in corresponding standard operating procedures, and the requirements for the device should be included in the product specifications.
Priority levels
- Level 0 (“lay person level”)
Even most lay persons would meet this requirement. Anyone who does not even meet the requirements of this level should not develop medical devices. An auditor may and must expect these requirements to be met in the very first audit. - Level 1 (“advanced beginner level”)
The manufacturer has already addressed the issue of IT security. This level can be accepted for less critical devices and the first audits. However, improvement is expected each subsequent year until level 2 is reached. - Level 2 (“state of the art”)
This is the level that manufacturers generally have to achieve in the long term. However, it does not yet correspond to the state of the art. - Level 3 (“expert level”)
This level is achieved by full-time IT security experts. It goes beyond what an auditor can usually expect regarding medical devices. Energy suppliers, secret services and the military would have to operate at this level.
Why a guideline on IT security is needed
Numerous reasons led the authors to create the guideline:
- The EU regulations (MDR, IVDR) explicitly require IT security. Unlike most other essential requirements, there are no harmonized standards for IT security. Therefore, no canonical catalog of requirements reflects the required state of the art in a recognized way.
- For this reason, auditors have very heterogeneous expectations, and manufacturers are more likely to encounter problems in the audit or when submitting documents.
- Many standards are chargeable (despite their sometimes questionable quality). The authors believe manufacturers must have free access to regulatory requirements.
- Manufacturers are developing more and more networked medical devices. This increases risks due to a lack of IT security (e.g., against cyber-attacks). Many manufacturers do not take this into account sufficiently.
- For most manufacturers, it would be neither time-consuming nor financially feasible to achieve the level of IT security required by UL 2900, for example, in one fell swoop. Manufacturers should, therefore, gradually strive to achieve a state-of-the-art level of IT security. The objective of this guideline is thus to implement initial improvements quickly rather than doing nothing because of excessive demands.
It is to be expected that standards for the IT security of medical devices will be developed and harmonized, but this may still take years. A guideline is therefore (only) needed in this interim phase.
A complete overview of the recitals can be found at the end of the document.
What happens next
In the long term (3-5 years?), the authors hope harmonized standards will make the IT Security Guideline superfluous. Until then, the guideline will continue to be updated. Everyone is invited to do so. “Complaining” does not help; participation is required. We look forward to your support. Please get in touch with the authors (e.g., at the Johner Institute).